Table of Contents
Production Environment
After an IdP/AA or SP has successfully passed the functional tests within the Test Federation (and all other requirements are met), the instance in question can be transferred to the production environment in two steps.
NB: Please note that the path names in the examples below refer to a Shibboleth installation under Debian GNU/Linux and have to be modified according to the actual local environment!
1. Metadata Administration Tool
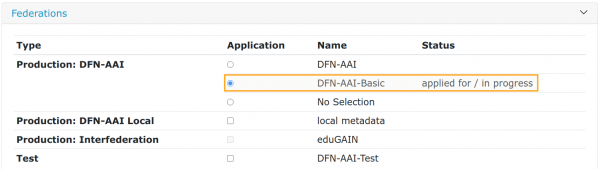
Using the Metadata Admin Tool (entity edit view, section “Federations”), the respective entity has to be added to the federation / metadata set(s) that is considered to fit best the needs for productive operations, i.e. at least DFN-AAI and - if applicable - eduGAIN. The system will check whether the metadata of this entity meet all requirements of the production environment (especially the registered certificate[s]) - and whether the account is linked with a contract. If the checks are positive, the button will be unlocked. The metadata entry in question is then reviewed by the DFN-AAI team.
2. Configuration Changes
In order to be able to communicate with other entities in the production environment, the configuration of the IdP/AA or SP has to be adjusted accordingly.
MetadataProvider
NB: As for the certificate used for metadata signature validation, the examples below refer to the hierarchy of the DFN-PKI second generation. Please refer to Metadata.
SP Operators include the metadata file that comprises all IdPs registered with the DFN-AAI production environment.
IdP Operators include the metadata file that comprises all SPs registered with the DFN-AAI production environment.
The page Metadata gives an overview of the available metadata sets/aggregates.
| IdP / AA | SP | |
|---|---|---|
| DFN-AAI | dfn-aai-sp-metadata.xml | dfn-aai-idp-metadata.xml |
| eduGAIN | dfn-aai-edugain+sp-metadata.xml | dfn-aai-edugain+idp-metadata.xml |
| Local Metadata | dfn-aai-local-999-metadata.xml* | dfn-aai-local-999-metadata.xml* |
(* Please refer to the remarks and examples at Local Metadata)
IdP Example
For metadata URLs and the certificate for signature validation please refer to the Metadata documentation.
DFN-AAI: Cf. Federation Metadata (de).
For participation in eduGAIN, the entity must consume a separate metadata set in addition to the DFN-AAI federation metadata:
- ./conf/metadata-providers.xml
<?xml version="1.0" encoding="UTF-8"?> <MetadataProvider id="ShibbolethMetadata" xsi:type="ChainingMetadataProvider" xmlns="urn:mace:shibboleth:2.0:metadata" xmlns:resource="urn:mace:shibboleth:2.0:resource" xmlns:security="urn:mace:shibboleth:2.0:security" xmlns:md="urn:oasis:names:tc:SAML:2.0:metadata" xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xsi:schemaLocation="urn:mace:shibboleth:2.0:metadata http://shibboleth.net/schema/idp/shibboleth-metadata.xsd urn:mace:shibboleth:2.0:resource http://shibboleth.net/schema/idp/shibboleth-resource.xsd urn:mace:shibboleth:2.0:security http://shibboleth.net/schema/idp/shibboleth-security.xsd urn:oasis:names:tc:SAML:2.0:metadata http://docs.oasis-open.org/security/saml/v2.0/saml-schema-metadata-2.0.xsd"> <!-- Metadata of all SPs in DFN-AAI production environment --> <MetadataProvider id="DFN_AAI" xsi:type="FileBackedHTTPMetadataProvider" backingFile="%{idp.home}/metadata/dfn-aai-sp-metadata.xml" metadataURL="http://www.aai.dfn.de/metadata/dfn-aai-sp-metadata.xml" maxRefreshDelay="PT2H"> <MetadataFilter xsi:type="SignatureValidation" requireSignedRoot="true" certificateFile="/etc/ssl/aai/dfn-aai.pem"/> </MetadataProvider> <!-- Metadata of all SPs in eduGAIN--> <MetadataProvider id="DFN_AAI_eduGAIN" xsi:type="FileBackedHTTPMetadataProvider" backingFile="%{idp.home}/metadata/dfn-aai-edugain+sp-metadata.xml" metadataURL="http://www.aai.dfn.de/metadata/dfn-aai-edugain+sp-metadata.xml" maxRefreshDelay="PT2H"> <MetadataFilter xsi:type="SignatureValidation" requireSignedRoot="true" certificateFile="/etc/ssl/aai/dfn-aai.pem"/> </MetadataProvider> </MetadataProvider>
SP Example
Important note: Make sure that redirectLimit is set to the value 'host' or 'exact'!
Please make sure that inshibboleth2.xml in all <Sessions> elements the XML attribute redirectLimit- is set and
- has the value
hostorexact! (if necessary in combination withallow)
This measure prevents the possible open redirect misuse of the SP e.g. in the context of a phishing attack, cf. https://shibboleth.atlassian.net/browse/SSPCPP-714.
For more information on the configuration parameters of the <Sessions> element see the Shibboleth Wiki.
For metadata URLs and the certificate for signature validation please refer to the Metadata documentation.
Communication with all productive IdPs in DFN-AAI as well as all IdPs from eduGAIN - except “Self-Signup” IdPs (cf. also Entity Attributes):
- /etc/shibboleth/shibboleth2.xml
<MetadataProvider type="XML" uri="http://www.aai.dfn.de/metadata/dfn-aai-idp-metadata.xml" backingFilePath="dfn-aai-idp-metadata.xml" reloadInterval="3600"> <MetadataFilter type="Signature" certificate="/etc/ssl/aai/dfn-aai.pem" /> </MetadataProvider> <MetadataProvider type="XML" uri="http://www.aai.dfn.de/metadata/dfn-aai-edugain+idp-metadata.xml" backingFilePath="dfn-aai-edugain+idp-metadata.xml" reloadInterval="3600"> <MetadataFilter type="Signature" certificate="/etc/ssl/aai/dfn-aai.pem" /> <MetadataFilter type="Exclude" matcher="EntityAttributes"> <saml:Attribute Name="http://macedir.org/entity-category" NameFormat="urn:oasis:names:tc:SAML:2.0:attrname-format:uri"> <saml:AttributeValue>http://aai.dfn.de/category/public-idp</saml:AttributeValue> </saml:Attribute> </MetadataFilter> </MetadataProvider>
Discovery Service
Embedded Discovery Service
In case an SP is only available for a couple of Home Organizations, we recommend to implement an Embedded Discovery Service that filters and lists only those IdPs that are relevant for the service/SP.
Central Discovery Service
In case no SP-specific and/or Embedded Discovery Service can be implemented, we provide a centralized discovery service as a fall-back. An SP can choose between several central discovery URLs in accordance with its MetadataProvider configuration (see above). So-called “Local SPs” that are intended for internal use only (e.g. campus management), should refer to the Entity ID of the IdP of the Home Organization (see also Local Metadata).
Examples for Shibboleth SP
Local IdP only
- /etc/shibboleth/shibboleth2.xml
<SSO entityID="https://idp.beispiel-uni.de/idp/shibboleth"> SAML2 </SSO>
All productive IdPs in DFN-AAI
- /etc/shibboleth/shibboleth2.xml
<SSO discoveryProtocol="SAMLDS" discoveryURL="https://wayf.aai.dfn.de/DFN-AAI/wayf"> SAML2 </SSO>
All productive IdPs in DFN-AAI and in eduGAIN
- /etc/shibboleth/shibboleth2.xml
<SSO discoveryProtocol="SAMLDS" discoveryURL="https://wayf.aai.dfn.de/DFN-AAI-eduGAIN/wayf"> SAML2 </SSO>