Table of Contents
Check list for publishing metadata
Access to the metadata administration tool
New metadata admins can be designated by the administrative or technical contacts who signed the contract with us (see the contract details in Metadata Admin tool). They can send us an e-mail to hotline@aai.dfn.de, containing the following contact details for each new metadata admin:- full name,
- e-mail address and
- work phone number.
The credentials will be sent directly to the new metadata admins.
Please have a look at the valid version of the Metadata Registration Practice Statements.
Before submitting a new IdP/SP to the federation, please make sure you have filled in the form as described below - that is: before you activate a federation with this radio button:
- Fill in all fields. If you see warnings correct them before submitting the IdP/SP to production.
- Use host name resp. URLs that can be resolved from outside your network. Systems with internal top level domains cannot be saved.
Entity ID
A unique string that globally distinguishes this entity from all other entities. The Entity ID is an absolute https-scheme URL. The federation participant has to make sure they are entitled to use the domain in the URL. See the Metadata Registration Practice Statement for details.
Examples:
Remark: With Shibboleth IdPs, the Entity ID is configured in ./conf/idp.properties, with Shibboleth SPs in /etc/shibboleth/shibboleth2.xml.
Important: You cannot change an Entity ID in this form! Doing so results in a copy of the whole entry being created. The old entity stays unless you explicitly delete it.
Display name
The element <mdui:DisplayName> contains a human-readable name of the service. Identity Providers' display names are shown in the selection menu of discovery services. Service Providers' display names are displayed on an IdP's login page and in the user consent dialogue. Ampersands must be entered as & !
Description
A short description for the public DFN-AAI directory and other services extracting human-readable information from federation metadata. Ampersands must be entered as & !
Information URL
Link to a page containing additional information about the service, resp. - with IdPs - about the organization.
Privacy Statement URL
Link to the privacy statement of the IdP or SP. For Service Providers the field is mandatory. If you only have a privacy statement in either English or German you can leave the second field blank.
Logo
Link to the logo and favicon if the organization resp. the service provider. An IdP favicon is displayed in the selection menu of discovery services. An SP logo is shown on IdP‘s login pages. SP metadata do not require a favicon. Requirements and recommendations:
- New logos and favicons must be uploaded to and served by the metadata administration tool. Logos should be 64 to 240 px wide and 48 to 180 px high.
- Favicons should have a size of 16 x 16 px.
- A transparent background is recommended.
Also see the recommendations in the Shibboleth Wiki.
Help Desk
Contact information of your user help desk for the public DFN-AAI directory (e.g. e-mail address, phone number).
Entity Category
For Entity Categories resp. Entity Attributes please see our Documentation.
Entity Category Support
Entity Attribute for an IdP to announce that it transmits all attributes defined in a certain Entity Category to all SPs using that Entity Category.
Contacts
Each entity's metadata should provide contact information for the following roles. If possible, it should not be personal e-mail addresses.
- administrative: contact information for administrative issues
- technical: contact information concerning the operation of the service
- support: contact information for end users
- security: contact information for security incidents.
Also see Choosing a Sirtfi Contact.
Scope
Scope of the IdP, mostly the domain of the organization. The organization has to be entitled to use the domain(s). SPs match the transmitted ‚scoped‘ attributes (e.g. eduPersonScopedAffiliation) against this string. See the Metadata Registration Practice Statement for details.
Request Initiator
Service Provider URL that initializes a login process.
Discovery Response
Service Provider URL the initializes IdP discovery.
Certificates
Enter the certificates used to sign resp. encrypt the SAML communication (in pem format). Check the certificate details before hitting the save button. Note that every IdP/SP has to publish a certificate for signing and encryption of SAML communication. Use can either use the same certificate for both (empty purpose field) or tow different certificates (select the purpose from the drop-down menu). Also see the detailed information about certificates, certificate rollover, and certificate chains.
For Service Providers (optional): If you need your SP to execute Attribute Queries or Artifact Queries, your SP certificate should have the client attribute set. If you request your certificate from DFN-PKI, please use the template called “Shibboleth IdP/-SP”. If you do not use DFN-PKI certificates, have a look at our Swiss colleagues' documentation. If you do not need any Attribute/Artifact Queries, please deactivate the feature in your SP. With a Shibboleth SP you'd have to remove the element <AttributeResolver type=“Query”> and to restart shibd. Moreover, you should remove the Binding URL for Artifact Resolution Services and all SOAP Bindings (Logout). Here is how you check if your certificate has the client attribute set with openssl:
openssl x509 -in example.org.crt.pem -noout -text | grep -A 1 "X509v3 Extended Key Usage"
X509v3 Extended Key Usage:
TLS Web Client Authentication, TLS Web Server Authentication
Single Logout Services
IdPs and SPs supporting Single Logout Requests have to publish the respective endpoints here.
Example for Shibboleth IdPs:
https://idp.example.org/idp/profile/SAML2/Redirect/SLO urn:oasis:names:tc:SAML:2.0:bindings:HTTP-Redirect https://idp.example.org/idp/profile/SAML2/POST/SLO urn:oasis:names:tc:SAML:2.0:bindings:HTTP-POST https://idp.example.org/idp/profile/SAML2/POST-SimpleSign/SLO urn:oasis:names:tc:SAML:2.0:bindings:HTTP-POST-SimpleSign https://idp.example.org:8443/idp/profile/SAML2/SOAP/SLO urn:oasis:names:tc:SAML:2.0:bindings:SOAP
Example for Shibboleth SPs:
https://sp.example.org/Shibboleth.sso/SLO/SOAP urn:oasis:names:tc:SAML:2.0:bindings:SOAP https://sp.example.org/Shibboleth.sso/SLO/Redirect urn:oasis:names:tc:SAML:2.0:bindings:HTTP-Redirect https://sp.example.org/Shibboleth.sso/SLO/POST urn:oasis:names:tc:SAML:2.0:bindings:HTTP-POST https://sp.example.org/Shibboleth.sso/SLO/Artifact urn:oasis:names:tc:SAML:2.0:bindings:HTTP-Artifact
Assertion Consumer Services
Endpoints of an SPs Assertion Consumer Service. Examples:
Location: https://example.org:8443/Shibboleth.sso/SAML2/POST Binding: urn:oasis:names:tc:SAML:2.0:bindings:HTTP-POST Index: 1
Location: https://example.org:8443/Shibboleth.sso/SAML2/POST-SimpleSign Binding: urn:oasis:names:tc:SAML:2.0:bindings:HTTP-POST-SimpleSign Index: 2
Location: https://example.org:8443/Shibboleth.sso/SAML2/Artifact Binding: urn:oasis:names:tc:SAML:2.0:bindings:HTTP-Artifact Index: 3
Location: https://example.org:8443/Shibboleth.sso/SAML2/ECP Binding: urn:oasis:names:tc:SAML:2.0:bindings:PAOS Index: 4
Attribute Consuming Service
List of attributes the SP takes.
Artifact Resolution Services
Example:
Location: https://idp.example.org:8443/idp/profile/SAML2/SOAP/ArtifactResolution Binding: urn:oasis:names:tc:SAML:2.0:bindings:SOAP Index: 1
Single Sign On Services
Single Sign On end points of an IdP. Examples:
Location: https://idp.example.org/idp/profile/SAML2/POST/SSO Binding: urn:oasis:names:tc:SAML:2.0:bindings:HTTP-POST Location: https://idp.example.org/idp/profile/SAML2/POST-Simple-Sign/SSO Binding: urn:oasis:names:tc:SAML:2.0:bindings:HTTP-POST-Simple-Sign Location: https://idp.example.org/idp/profile/SAML2/Redirect/SSO Binding: urn:oasis:names:tc:SAML:2.0:bindings:HTTP-Redirect
Attribute Services
IdP end points for Attribute Query via SOAP Requests. Example:
Location: https://idp.example.org:8443/idp/profile/SAML2/SOAP/AttributeQuery Binding: urn:oasis:names:tc:SAML:2.0:bindings:SOAP
NameID Formats
Supported NameID formats. At least urn:oasis:names:tc:SAML:2.0:nameid-format:transient should be selected. It is active in default installations and is needed for logout to work. Other formats should only be selected if they were explicitly activated in the configuration.
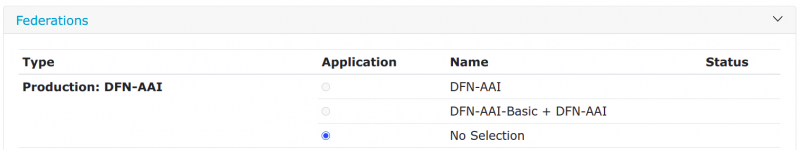
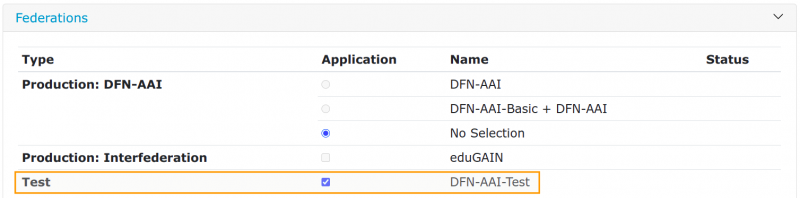
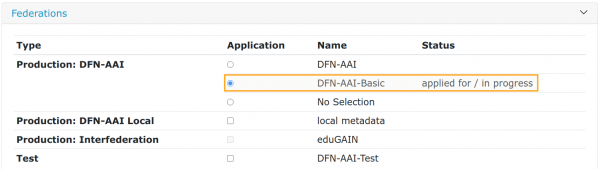
Federations
Here you add your IdP/SP to federations. If you submit your provider to DFN-AAI-Test or to local metadata, it is automatically added to the according metadata. Submissions for DFN-AAI and DFN-AAI-Basic are first checked by the DFN-AAI team. Admission is granted within a working day, unless the metadata form displays errors. Please fix these errors first! You can only add your IdP/SP to the international federation eduGAIN after it has been accepted to either DFN-AAI or DFN-AAI-Basic. You can find our policies in the documentation
Information regarding the Degrees of Reliance:
IdP:
- Depending on the criteria your IdP fulfills add it to either DFN-AAI or DFN-AAI-Basic.
- In addition, an IdP can be registered in DFN-AAI-Test and in local metadata. Keeping a productive IdP in the test federation is not recommended.
SP:
- Choose the degree of reliance that an IdP (!) must fulfill to grant access to their users. In DFN-AAI only users of the 'Advanced' degree of reliance can access the SP. In DFN-AAI-Basic the users of all IdPs in the federation can access it.
- Additionally, the SP can be registered in DFN-AAI-Test. A productive SP should not be in the test federation to prevent logins from test IdPs.
- Local metadata can only be selected if neither DFN-AAI nor DFN-AAI-Basic is selected. The option is available for organizations that have signed an IdP contract with us and have registered at least an IdP.
- Put your new system into our test federation DFN-AAI-Test. Use our public test systems to check if the transfer of attributes works correctly.
- If it does, submit a request to join DFN-AAI. A ticket is then opened on our side and you will hear from us.